-
Notifications
You must be signed in to change notification settings - Fork 113
Authentication
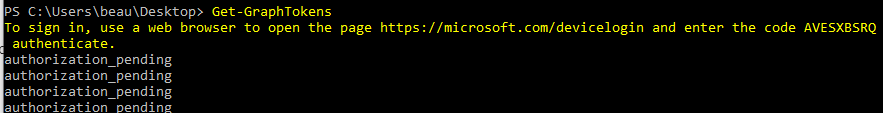
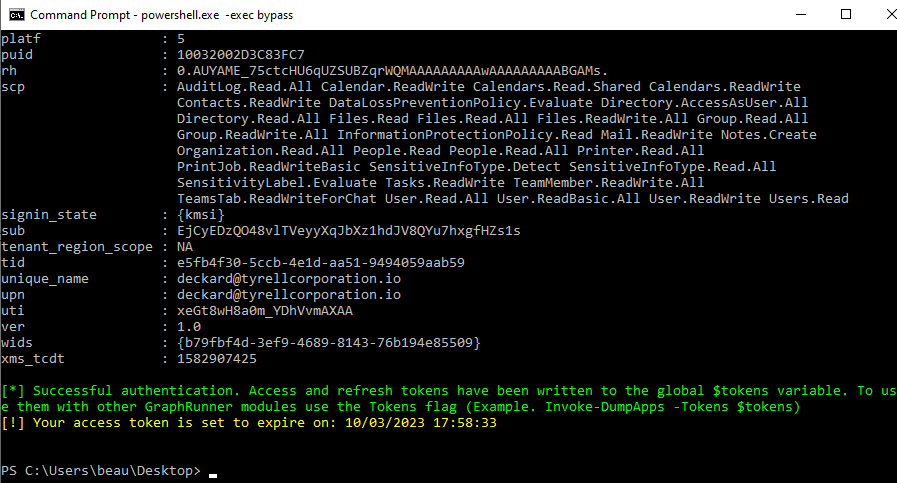
A good place to start is to authenticate with the Get-GraphTokens module. This module will launch a device-code login, allowing you to authenticate the session from a browser session. Access and refresh tokens will be written to the global $tokens variable. To use them with other GraphRunner modules use the Tokens flag (Example. Invoke-DumpApps -Tokens $tokens)
--OPTIONS--
UserPasswordAuth - Provide a username and password for authentication instead of using a device code auth. (User will be prompted)
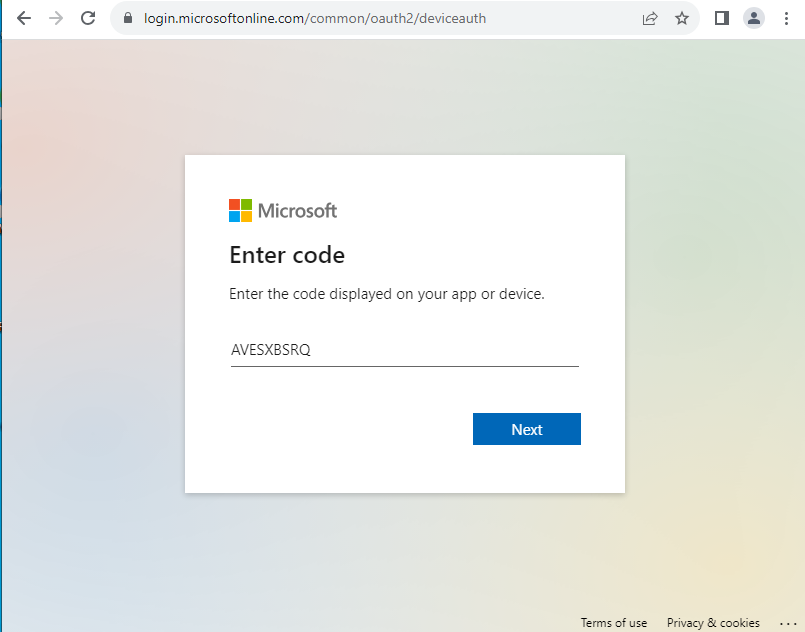
Get-GraphTokensAfter running Get-GraphTokens perform a device code auth at microsoft.com/devicelogin with the provided code.
After completing the device code auth GraphRunner should set the tokens to the $tokens variable.
Access tokens typically have an expiration time of one hour so it will be necessary to refresh them occasionally. If you have already run the Get-GraphTokens command your refresh tokens will be utilized when you run Invoke-RefreshGraphTokens to obtain a new set of tokens.
--OPTIONS--
TenantId - The Tenant ID where the token is being refreshed
RefreshToken - A refresh token from an authenticated session
Invoke-RefreshGraphTokensThis module can assist with completing an OAuth flow to obtain access tokens for an Azure App Registration. After obtaining an authorization code it can be utilized with a set of app registration credentials (client id and secret) to complete the flow.
--OPTIONS--
ClientId - The Client ID (AppID) of the App
ClientSecret - The Secret of the App
RedirectUri - The Redirect URI used in the authorization request
Scope - Permission scope of the app "Mail.Read openid etc"
AuthCode - The authorization code retrieved from the request sent to the redirect URI during the OAuth flow
Get-AzureAppTokens -ClientId "13483541-1337-4a13-1234-0123456789ABC" -ClientSecret "v-Q8Q~fEXAMPLEEXAMPLEDsmKpQw_Wwd57-albMZ" -RedirectUri "https://YOURREDIRECTWEBSERVER.azurewebsites.net" -scope "openid profile offline_access email User.Read User.ReadBasic.All Mail.Read" -AuthCode "0.AUYAME_74EXAMPLEUZSUBZqrWXZOtU7Jh4..."This module refreshes an Azure App token.
--OPTIONS--
ClientId - The Client ID (AppID) of the App
ClientSecret - The Secret of the App
RedirectUri - The Redirect URI used in the authorization request
Scope - Permission scope of the app "Mail.Read openid etc"
RefreshToken - A refresh token from an authenticated session
Invoke-RefreshAzureAppTokens -ClientId "13483541-1337-4a13-1234-0123456789ABC" -ClientSecret "v-Q8Q~fEXAMPLEEXAMPLEDsmKpQw_Wwd57-albMZ" -RedirectUri "https://YOURREDIRECTWEBSERVER.azurewebsites.net" -scope "openid profile offline_access email User.Read User.ReadBasic.All Mail.Read" -RefreshToken "0.AUYAME_75cEXAMPLEUBZqrWd22WdOz..."Refresh tokens at an interval
--OPTIONS--
RefreshToken - A refresh token from an authenticated session
tenantid - Supply a tenant domain or ID to authenticate to
RefreshInterval - Supply an interval in minutes to refresh the token. Default 5 minutes
InitializationDelay - Supply a delay before starting to refresh in minutes. Default is 0
OutFile - Supply file name to save to. This will overwrite the current file.
Invoke-AutoTokenRefresh - RefreshToken "0.A.." -tenantid "company.com" -Outfile .\access_token.txt