-
Notifications
You must be signed in to change notification settings - Fork 113
Potential Attack Path Examples
Beau Bullock edited this page Oct 20, 2023
·
5 revisions
GraphRunner has a lot of different modules that do specific tasks but combining them can lead to interesting attack paths in certain scenarios. Below are a few examples where GraphRunner may benefit you in identifying potential situations where it can be used for persistence, privilege escalation, data harvesting, and more within an M365 account.
- Identify groups that can be modified by current user (Get-UpdatableGroups)
- Determine current access level (Get-SharePointSites, Invoke-DumpCAPS, Check for subscription access, Invoke-GraphRecon -PermissionEnum, etc.)
- Inject your user into the group (Invoke-AddGroupMember)
- Re-run enumeration modules to see if there is new access to sites/policies.
Bonus
Guest users can be injected into groups too but your current user (Entra ID user in the target tenant) needs to be injected first.
- Identify dynamic groups (Get-DynamicGroups) that have rules that can be abused such as a rule that adds a user to a group if their email contains “admin”.
- Analyze membership rules to determine if they can be abused.
- Example: Invite guest user to tenant with an email that has “admin” in the email address to get added as a member of a group where UPN’s that contain “admin” get automatically added to it.
- Identify an interesting group (SharePoint Admins, Dev groups, other IT groups, etc.)
- Clone it and add your own user (Invoke-SecurityGroupCloner)
- Wait for an admin to mistakenly add your cloned group to a policy somewhere OR come up with a ruse to get it added
- Monitor access to various M365 pieces like SharePoint, Teams, CAPS policies, subscriptions, etc.
- Inject an OAuth App registration (Invoke-InjectOAuthApp) into the same tenant as the compromised user.
- Setup a listener to complete the OAuth flow with either Invoke-AutoOAuthFlow to catch the redirect on your localhost or the AutoOAuthFlow.py script to catch it on another server.
- After consenting to the app it will generate tokens associated with the app registration that can be leveraged for accessing M365 as the user.
- If the user changes their password you still have access as the app.
- If all sessions get killed the refresh token of the app is still valid until it expires (default is 1 hour from creation time)
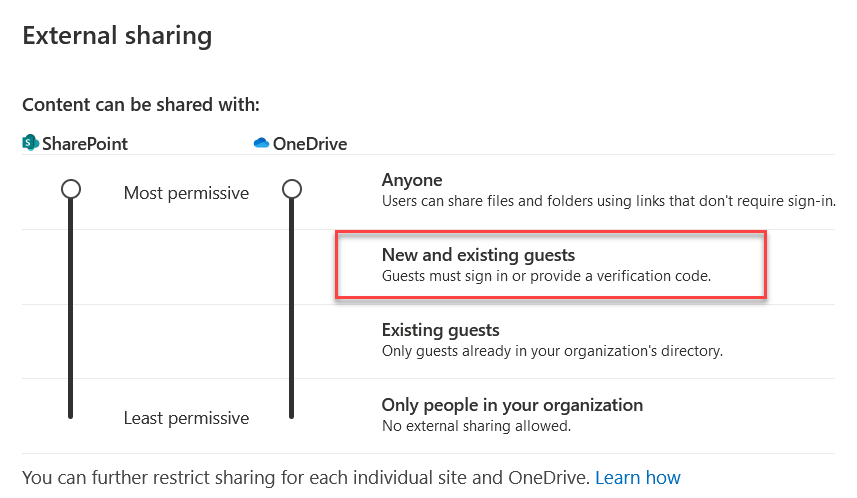
If external sharing for a site is set to allow “Anyone” or “New and existing guests” access via external sharing then it may be possible to leverage a guest account for long term access to specific files.
- Invite guest user to tenant (Invoke-InviteGuest).
- Gather SharePoint share links and maintain long term access to files until guest user is removed.
- Inject an OAuth app (Invoke-InjectOAuthApp) that has limited permissions (Mail.Read) into the same tenant as the compromised user.
- Use it to perform illicit consent grant phishing attacks internally for more access.
- Deploy an app with the “Mail.Read.Shared” scope into the victim tenant and consent to it with your user, or consent to this permission on the Graph Explorer and leverage the app token with GraphRunner.
- Use Invoke-GraphOpenInboxFinder to find other mailboxes that have been shared with you.
- Use Get-Inbox to pull the latest messages from other inboxes you can read.
- Leverage the pillage modules to identify sensitive data sent in email (Invoke-SearchMailbox, Get-Inbox), Teams chat (Invoke-SearchTeams, Get-TeamsChat) or SharePoint (Invoke-SearchSharePointAndOneDrive).
- Use the following command to perform “Snaffler-like” scanning of a SharePoint site:
- Invoke-GraphRunner -Tokens $tokens -DisableRecon -DisableUsers -DisableGroups -DisableCAPS -DisableApps -DisableEmail -DisableTeams
- Leverage the Invoke-SearchUserAttributes module to identify potentially sensitive information in Entra ID user attributes.
- Use Invoke-SearchSharePointAndOneDrive to identify interesting files
- Use Invoke-ImmersiveFileReader to download them in some environments that block file downloads from SharePoint and OneDrive.
- Gather a refresh token from an authenticated session (Ex. intercept browser)
- Use it with the Invoke-BruteClientIDAccess module to find applications that can authenticate or be refreshed to, along with their associated permission scopes.